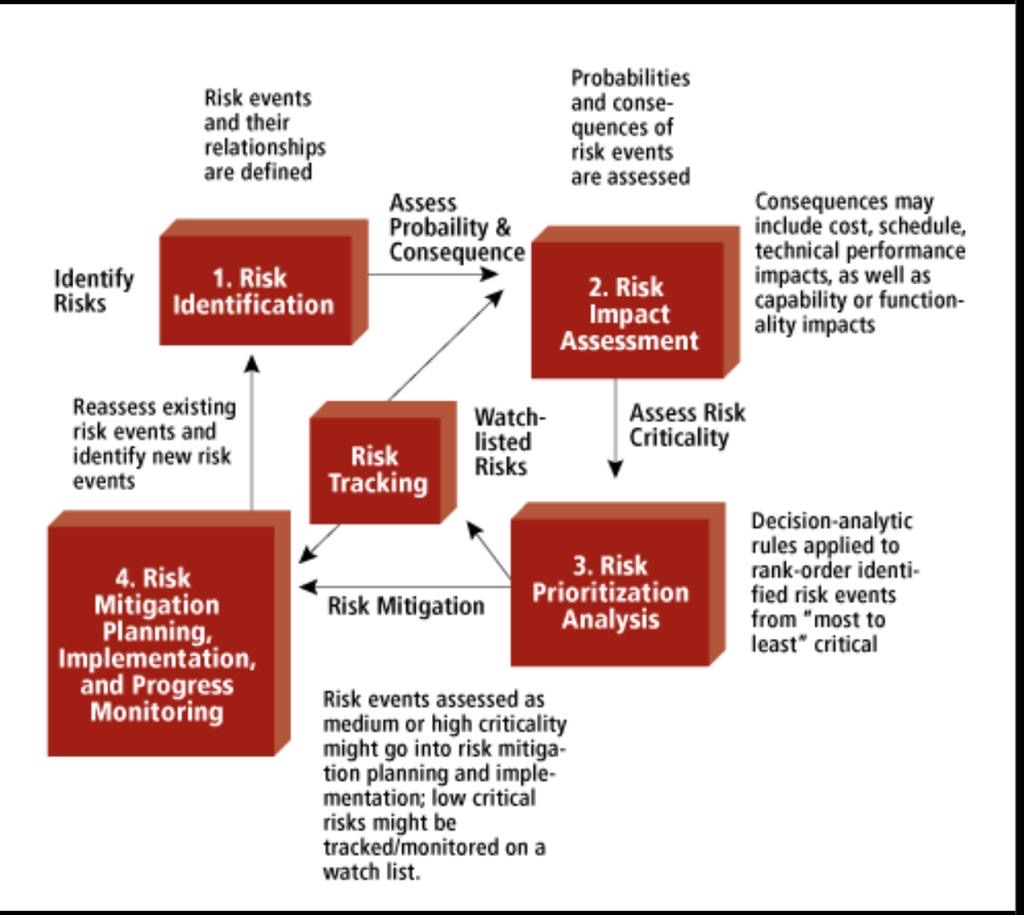
One of the biggest components in successfully managing your cybersecurity programs is a strong risk management plan. In order to successfully mitigate risks, they must be prioritized based on their overall effect on the organization. The major keys to reducing the impact of any risk to a project are to recognize, prioritize, and control.
Recognizing Risk
Accepting that despite the best laid plans, unforeseen conditions, design errors and omissions, and owner scope revisions will occur is imperative during the risk recognition process.
Prioritizing
Since every project is unique, the priorities of certain risks will be different for every project.
1) Identify: listing every potential risk to the project is necessary before any assessments can take place. Even events that have only a slight chance of occurring should be considered when creating the beginnings of your Risk Matrix.
2) Measure Likelihood: Each risk identified should be given a ranking based on the likelihood of them occurring. The scale for this ranking is at the discretion of the project team, it could be 1-5 with 1 being unlikely and 5 being likely, or it could be on a likelihood percentage basis.
3) Assess Impact: Using the same guidelines established when calculating likelihood, the project stakeholders should next rank the impact of different risks.
4) Find the Overall Calculated Risk: Depending on the scale used to measure likelihood and impact, a formula can be put together to calculate the overall risk associated with a certain event. From there, the risks can be weighed low, medium, and high so that the team can determine which risks are priorities.
Controlling & Mitigation
Many projects begin in an organized manner with a strong Risk Matrix, and as the day to day management of the project carries on, it becomes harder to stay on top of this document. The failure to update the Risk Matrix is the most common reason that some risks seem to arise out of nowhere at the last minute. In order to have a successful risk management program, the Risk Matrix must be updated and controlled on a regular basis. Priorities will shift, impacts will change, and new risks will arise. If the Risk Matrix is consistently being evaluated, plans to mitigate the high likely high impact risks.
Mitigating the highest calculated risks does not completely deter them from occurring, but establishes a workarounds and contingencies to lessen the overall impact to the project.
Every project comes with risks, and risk events will occur no matter the initial plan. A solid risk management program is the best way to keep these risk factors low, keeping priorities in place for the good of the project. Stakeholders from all parties must be involved in contributing to the Risk Matrix early and regularly, which can be accomplished by following the three simple steps of recognizing, prioritizing, and controlling.
CENTRALEYEZER is one of the most powerful tools for risk management. Why? Because from the beginning we have the risk-based approach in all our processes and services.
Centraleyezer risk calculation is fully customizable and takes into consideration factors like asset importance to the business, network zone, individual severity, applied counter-measures, threat-intel information or exploitability of a vulnerability allowing a personalized risk prioritization adapted to each situation.
We are among the first to use this “philosophy”, which is now a standard in the industry.