
Risk-Based Management – Identifying and Prioritizing the Risks
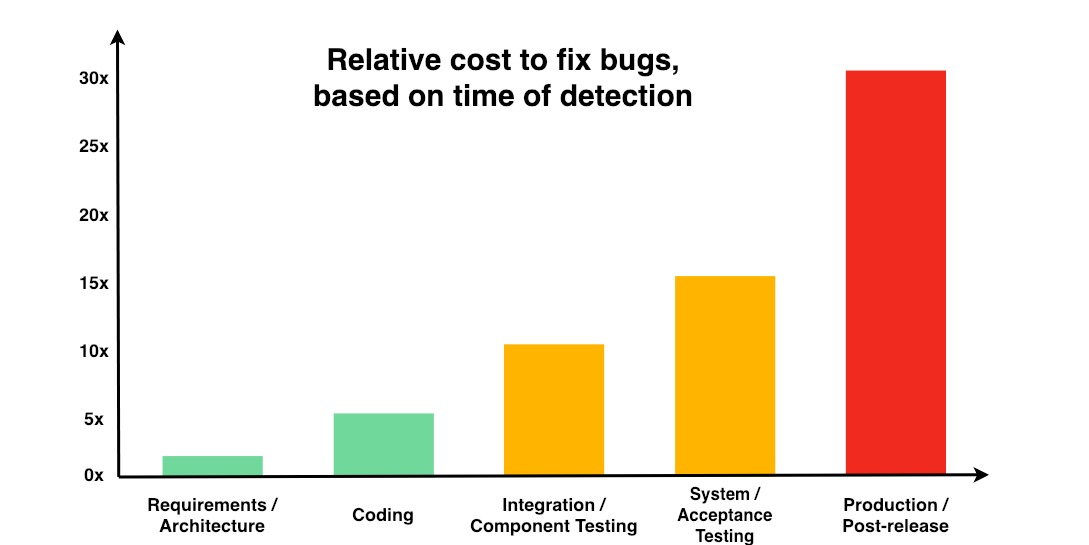
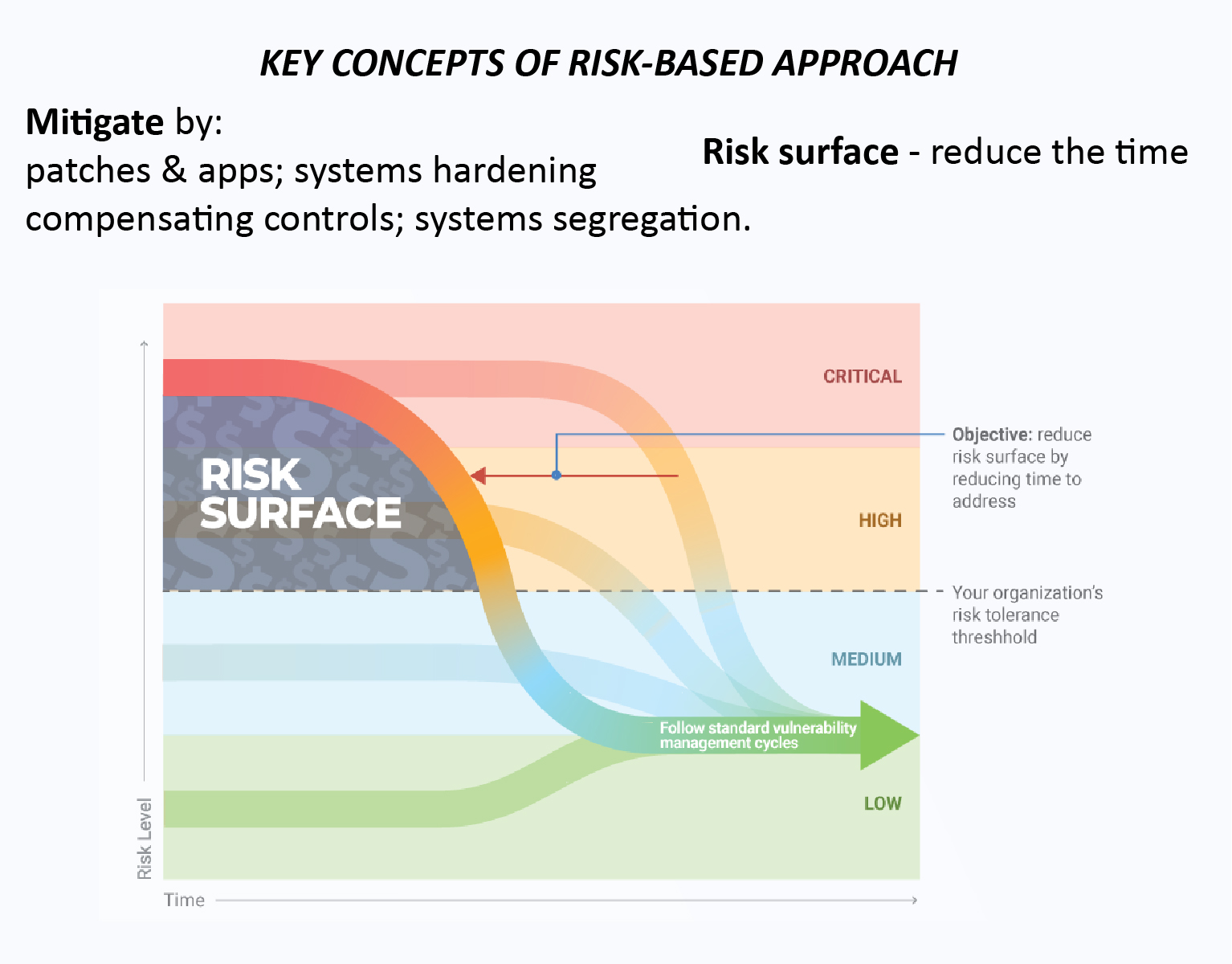
One of the biggest components in successfully managing your cybersecurity programs is a strong risk management plan. In order to successfully mitigate risks, they must be prioritized based on their overall effect on the organization. The major keys to reducing the impact of any risk to a project are to recognize, prioritize, and control. [...]



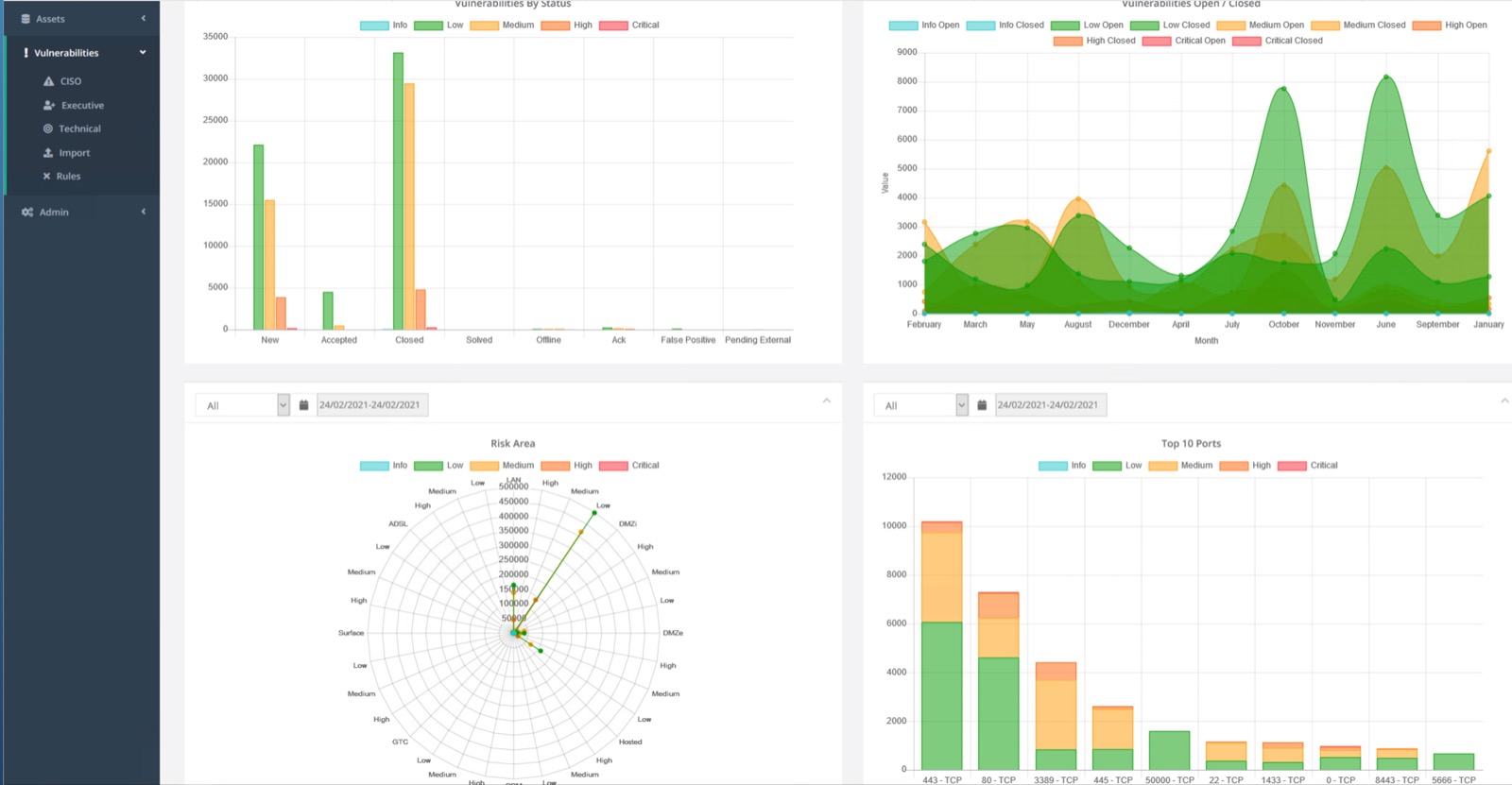
 A security red-team is a test that aims to assess the security level of an organization, identify main weaknesses in its security posture, provide insights about the organization’s resilience level, and reveal how prepared it is to withstand a real-life attack.
A security red-team is a test that aims to assess the security level of an organization, identify main weaknesses in its security posture, provide insights about the organization’s resilience level, and reveal how prepared it is to withstand a real-life attack.