From the time computing systems were first able to store large amounts of data, individuals with no right to that data have accessed it. When connectivity and breaches were rare, nobody cared.
But as more people and computers became connected, cybersecurity solutions and procedures have emerged to help organizations keep their data out of reach of threats.
That’s because all data are subject to a fundamental bias that comes from the era when the connectivity was scarce, but unfortunately is resilient until today: data cannot be simultaneously used and secured.
The reason is simple: All data, including applications, algorithms, and cryptographic keys, must sit exposed and unencrypted in memory so that the CPU can use them. This means anyone or any process that can get access to the host—including administrators, bad actors, or malware—can get full access to this data.
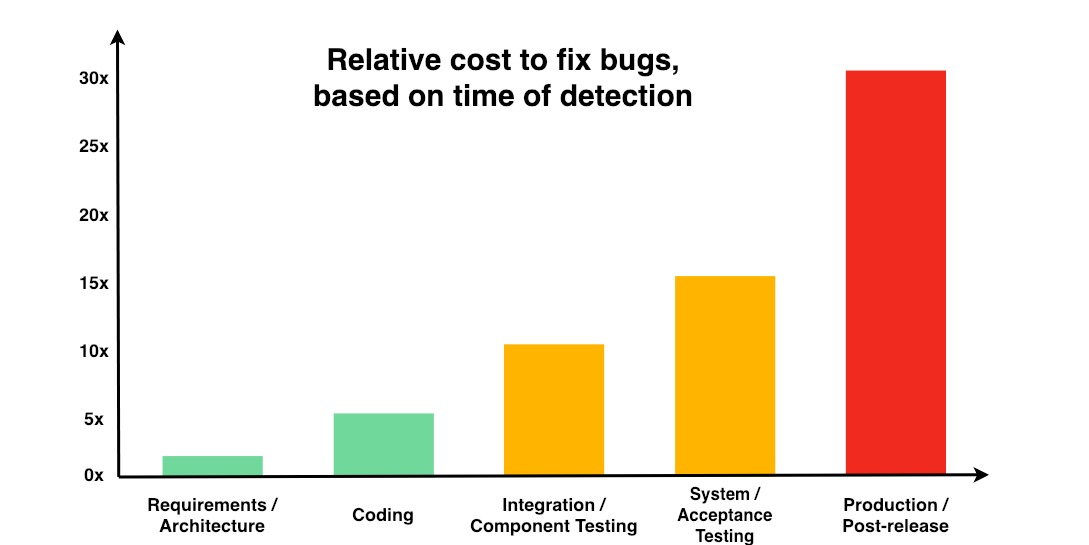
Many CISOs and business owners may not realize that this bias can cost their enterprises opportunities. Data exposure is one of the most repeated reasons for not migrating IT completely to the cloud, which is an option that can reduce IT costs and data risks.
Feeling the sweat on the forehead, the IT industry has moved to implement a long-accepted solution for this fundamental data flaw: secure enclaves.
Industry adoption has been broad. Secure enclave-enabled infrastructure is now available around the globe and deployed by every major cloud provider.
With all of these security advantages, you might think that CISOs would have quickly moved to protect their applications and data by implementing secure enclaves. But market adoption has been limited by a number of factors.
First, using the secure enclave protection hardware requires a different instruction set, and applications must be re-written and recompiled to work.
While secure enclave technologies do a great job protecting memory, they don’t cover storage and network communications – resources upon which most applications depend.
Another limiting factor has been the lack of market awareness. Server vendors and cloud providers have quickly embraced the new technology, but most IT organizations still may not know about them.
CISOs must be rescued
Simplifying and focusing on secure enclave solutions is now the domain and responsibility of a group of new and emerging secure enclave group of providers such as SANDLINE. We are now focusing on taking the raw silicon-level capabilities implemented by hardware and cloud providers and transforming them into something that is simple to adopt and use – without the need to rewrite software.
Foremost of these features is enclave technology independence, eliminating the need for multiple application rewrites. Another feature extends enclave protections to storage and networked communications, which will allow for broad application support without requiring modification.
Most importantly, this will result in the highest data security available, the rationalization of security layers for massive savings, and the next generation of exciting new applications to come in the future.
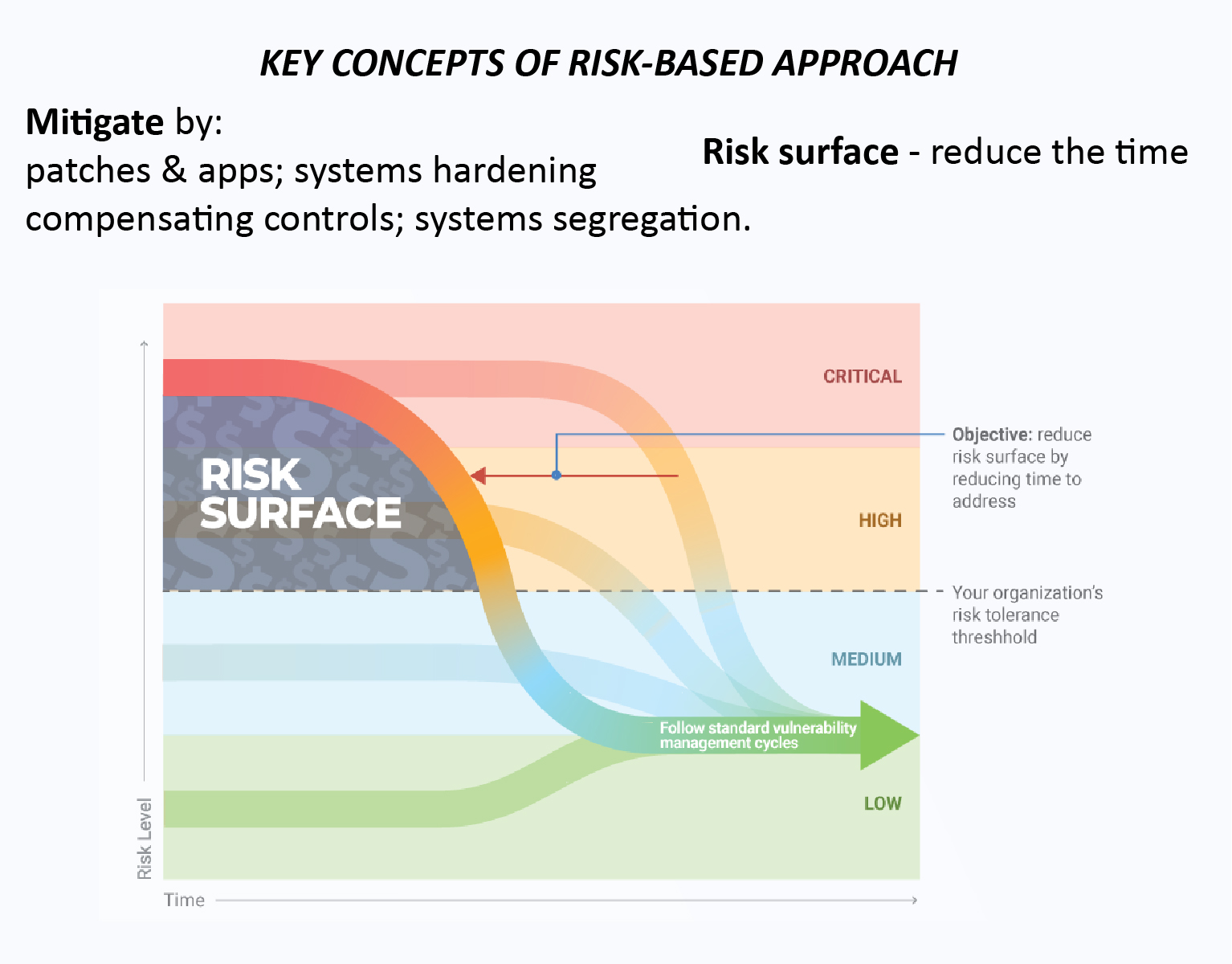
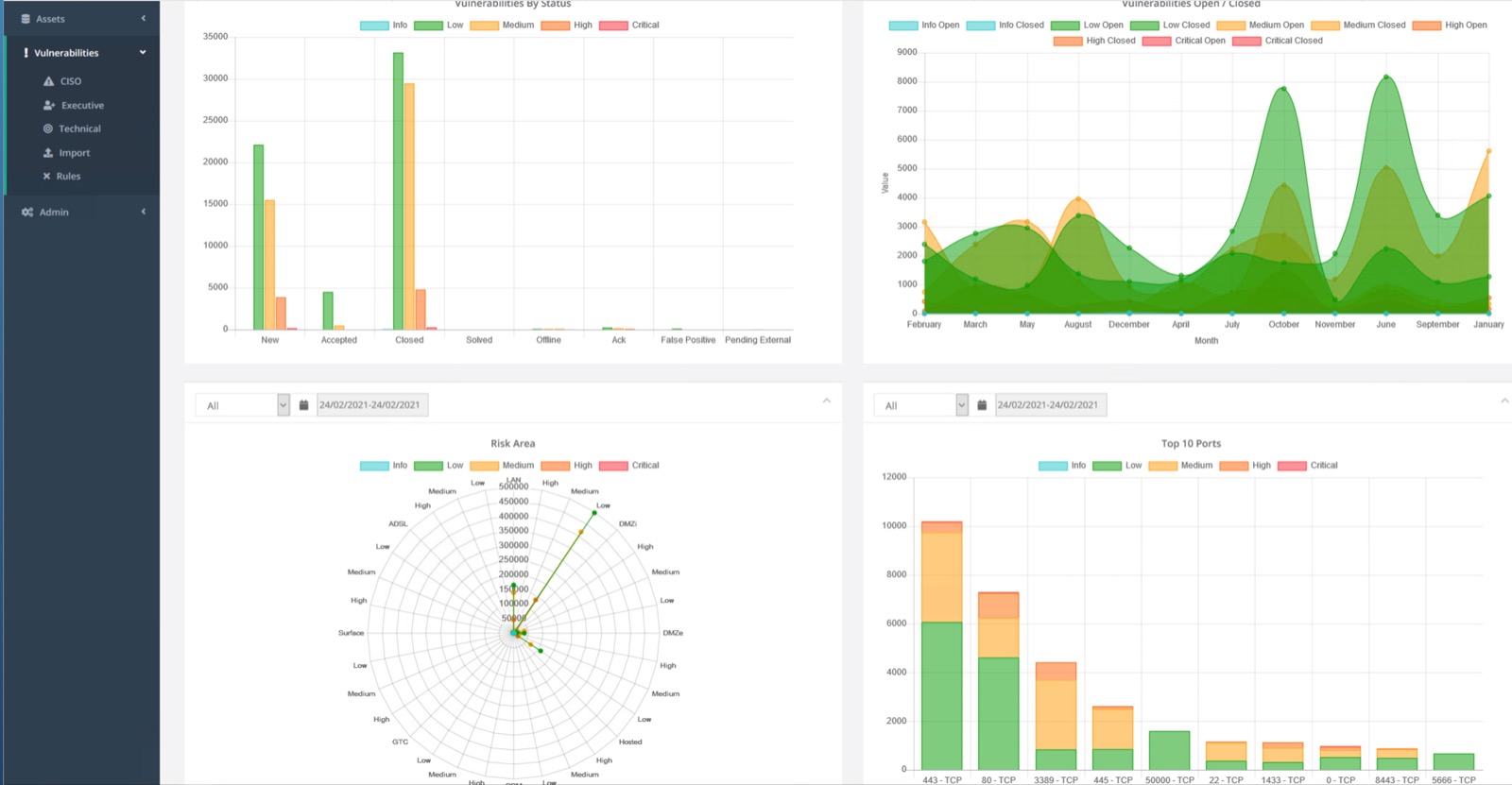
Data access is and should be a major part of the risk management strategy. SANDLINE is in the first line of a new cybersecurity best practice: risk-based approach to keep the businesses secured.