Some years ago we started at SANDLINE to become aware that a new shift in vulnerability management is necessary in order to tackle the more and more sophisticated methods of cyber-perpetrators.
Our response was CENTRALYEZER! The first professional tool built on the risk-based approach. Now, we are glad to see that our vision was right. More and more the industry is shifting to this paradigm.
Unlike common vulnerability management, risk-based vulnerability management goes beyond just discovering vulnerabilities. It helps you understand vulnerability risks with threat context and insight into potential business impact.
Why risk-based approach?
What we have found is that vulnerability management is not only patching management. Patching is only one aspect.
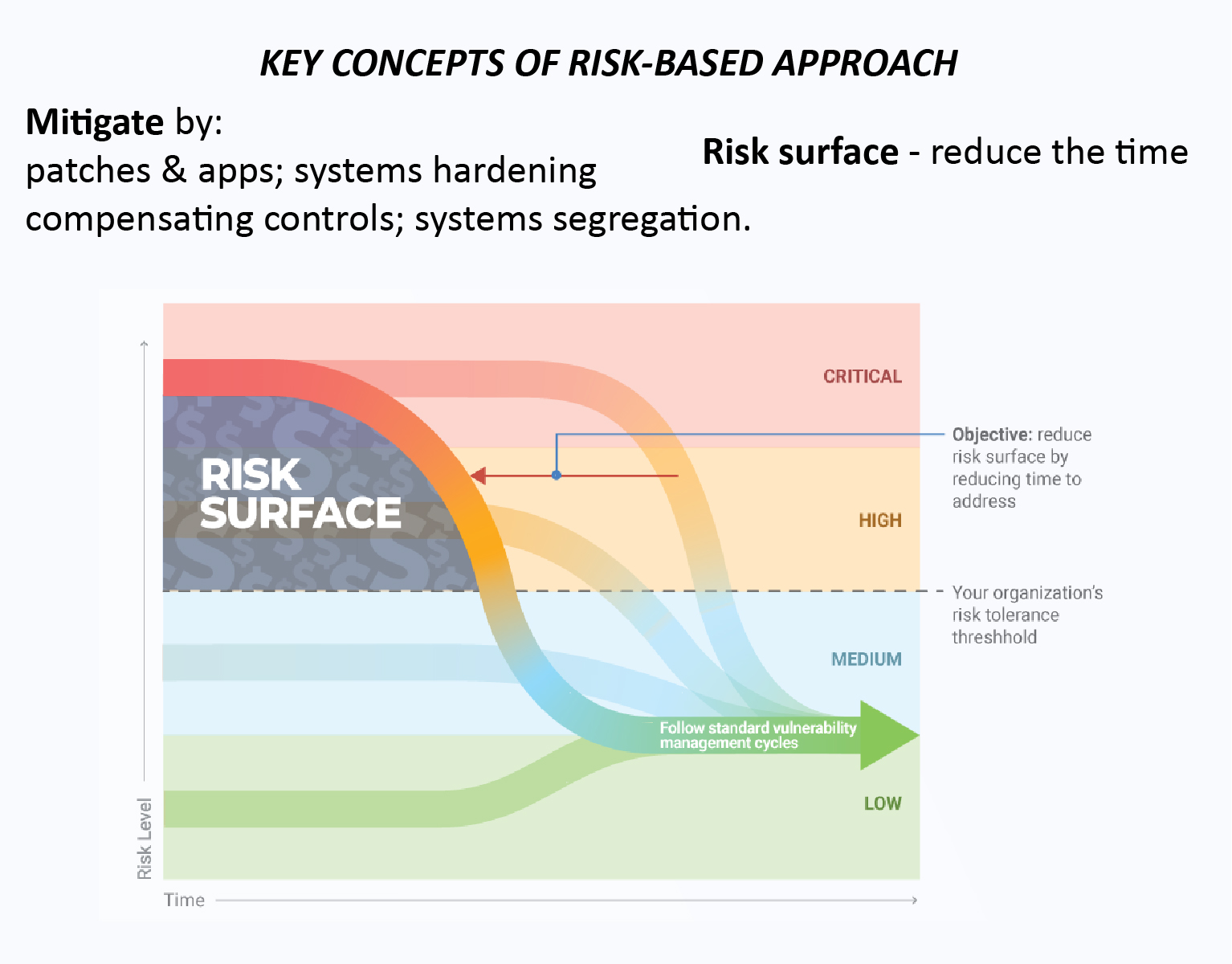
Taking a risk-based approach will allow you to focus on mitigating risk, rather than “just covering holes” in your environment.
The vulnerability management market is relatively mature; however, vulnerability management remains a very relevant and challenging topic.
Security practitioners are flooded with the advice they need to prioritize their vulnerabilities. Every vulnerability scanning provider will sustain their ability to prioritize the identified vulnerabilities.
This approach can create barriers that make vulnerability management difficult to address for many organizations. Besides, there are some obstacles in the very core of some organizations’ management: many feel that an “patching everything” approach is the most effective path or, vulnerability management is commonly misunderstood as being a process that only supports patching management.
Vulnerabilities are too numerous for manual scanning and detection.
Vulnerability management is not only the awareness of the existence of vulnerabilities, but that they are actively present in your environment.
A vulnerability scanner will usually report dozens, if not hundreds, of vulnerabilities on a regular and recurring basis. Typical IT environments have several dozen, if not hundreds, of servers. We haven’t even considered the amount of network equipment or the hundreds of user workstations in an environment.
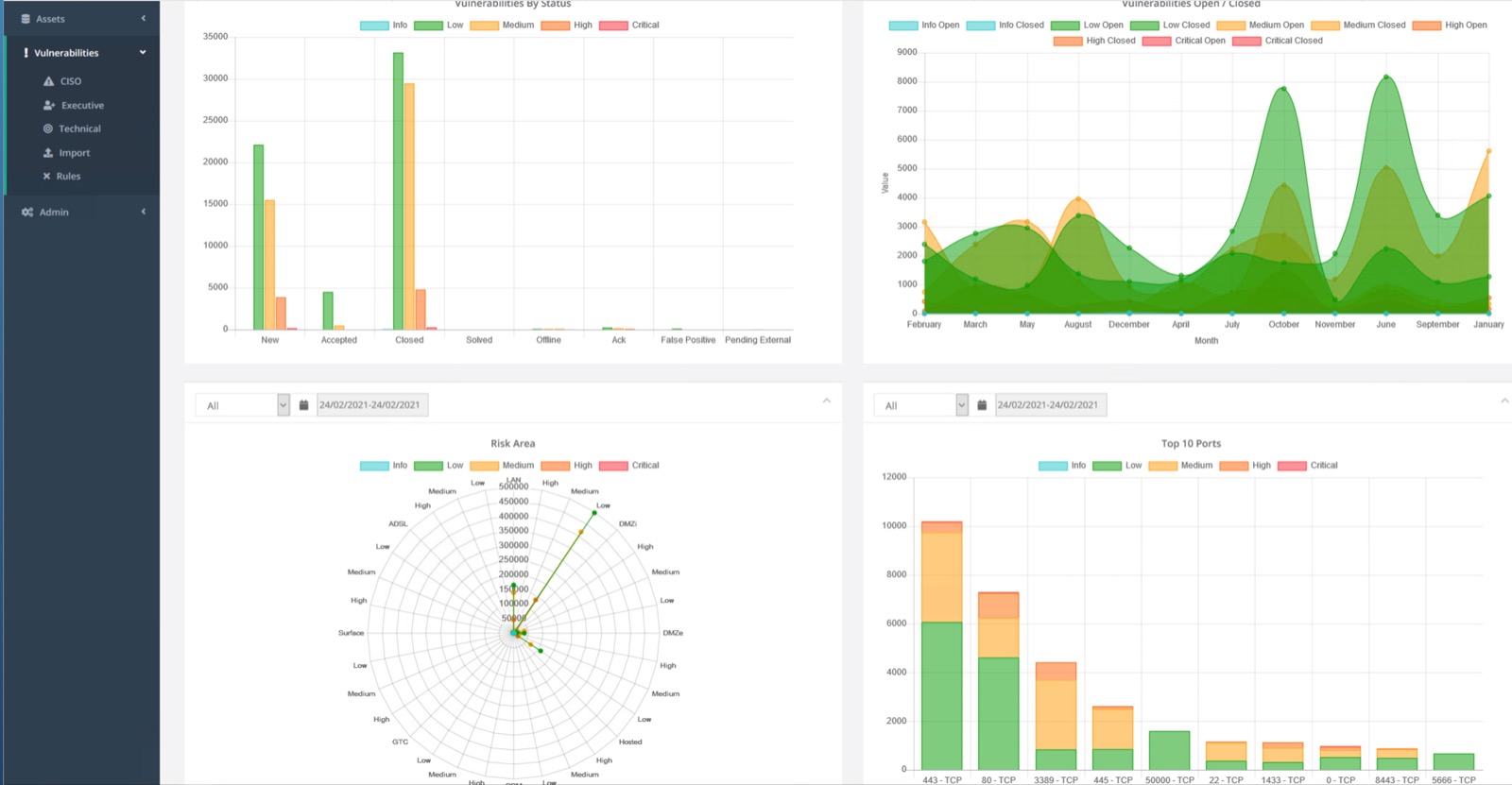
CENTRALEYEZER is the tool that will give you information on the risk of a vulnerability in your environment and the host on which the vulnerability exists. This includes a lot of other important information which will help you prioritize the remediation process based on real risks posed to your organization.
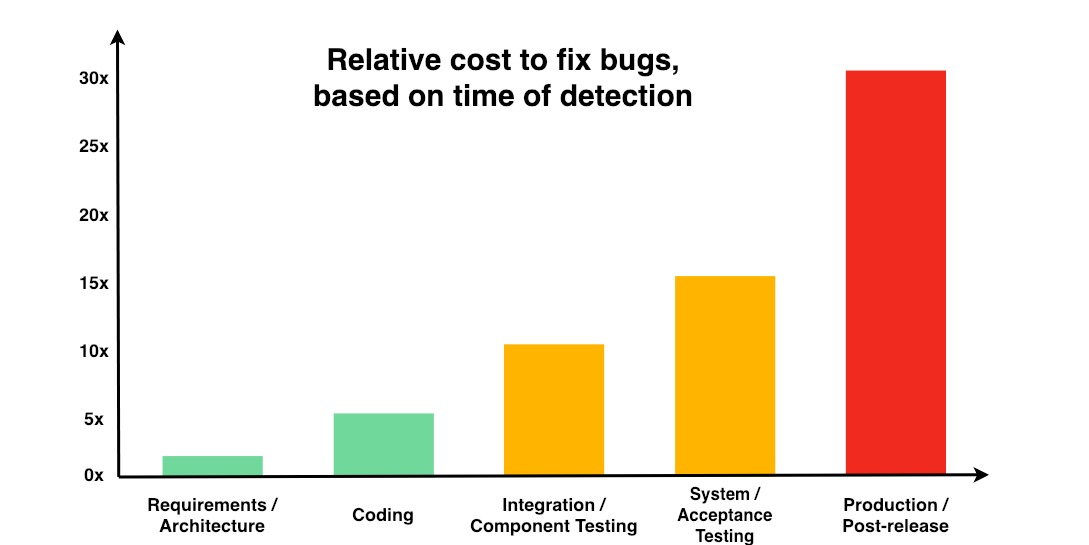
However, we must emphasize that vulnerability scanning is a valuable function, but it does not tell the full picture. You must determine how urgent a vulnerability truly is, based on your specific environment. So, you need to have the full picture, which only a professional and complete tool can offer at a glimpse.
Assessing a vulnerability’s risk will enable you to properly determine the true urgency of a vulnerability within the context of your organization; this ensures you are not just blindly following what the tool is reporting.
The risk-based approach will allow you to prioritize your discovered vulnerabilities and take immediate action on critical and high vulnerabilities while allowing your standard remediation cycle to address the medium to low vulnerabilities.
Lastly, while vulnerability management will help address your systems and applications, how do you know if you are secure from external malicious actors?
Penetration testing will offer visibility, allowing you to plug those holes and attain an environment with a smaller risk surface. CENTRALEYEZER gathers all the information from various sources in one place. It doesn’t matter the information is from scanner, pentests or other sources: you have one single point to overview/ track and manage.
The conclusion is that the risk-based approach is telling your organization exactly what it needs in order to be safe.