With the proliferation of high-profile hacks, data breaches and ransomware, it’s easy to feel insecure about your organization’s security these days. You have to protect your organization and its reputation like never before — particularly as your infrastructure grows and diversifies, presenting a broader front for attackers.
Still, not all security issues have to do with purposeful hacks and attacks. For many IT teams, the challenge is maintaining strict rules and regulatory requirements for everything from credit card data to health information privacy. Failing to maintain compliance can put your organization at risk of everything from lost business to substantial fines — or worse.
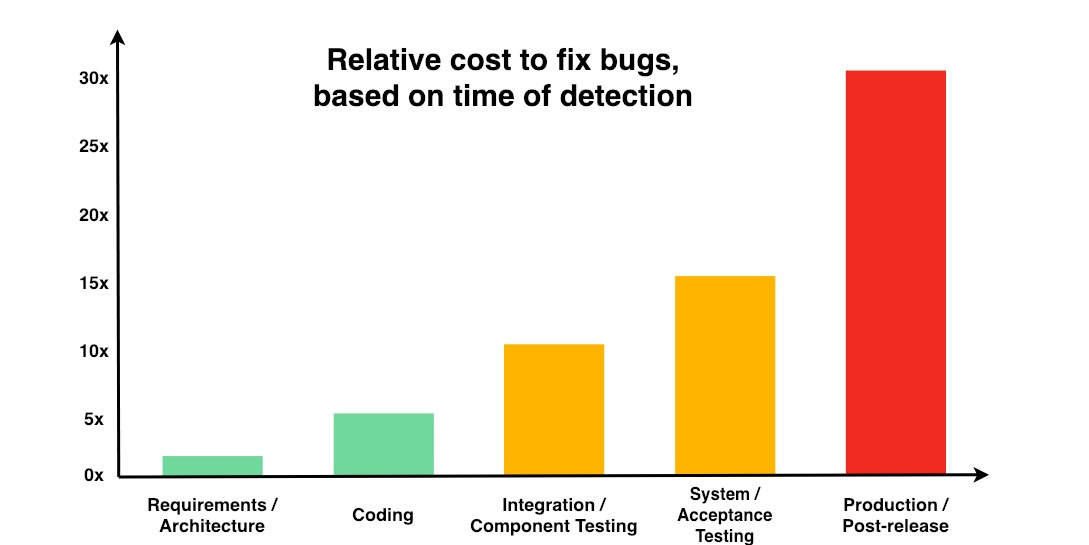
The most important approach is that your organization use IT automation to boost security and adopt continuous compliance as part of your DevSecOps workflow.
SANDLINE can offer you:
• Build a baseline of security rules and compliance requirements across your entire infrastructure.
• Incorporate a security review into the development life cycle, rather than leaving security considerations to the end of it.
• Apply DevSecOps practices to your software development, and cut the time your team spends remediating security issues.
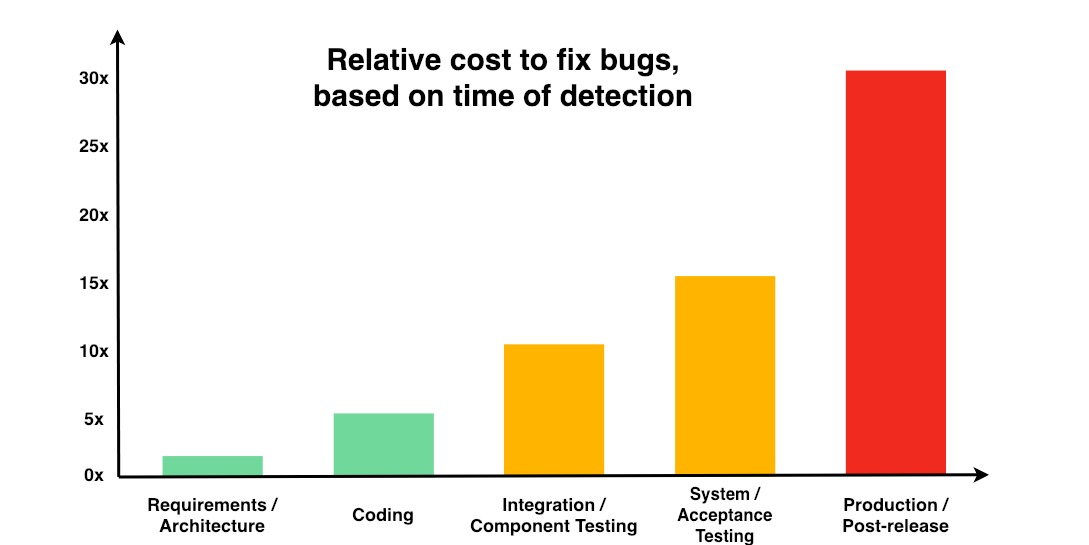
Back in the reality: your level of confidence in your overall security posture becomes less certain as time passes. You may well know what you put in place initially, and what you want to have in place continually, but you don’t necessarily know if every node and server is really in compliance. Perhaps you feel confident about your baselines when you first deploy servers databases and applications but what about a month out? Three months out? A year? The fact is, the longer it’s been since you deployed, the more vulnerable your servers become to anything from outdated patches to seemingly innocuous manual changes.
You also should consider the time involved in checking and proving compliance. Think of it this way: If you had to create a report for auditors showing who could log in to all the machines in your infrastructure — perhaps because of a breach — could you do it quickly? Would it take hours — or weeks? And what impact will this have on collaboration between ops and security teams as the clock ticks on?
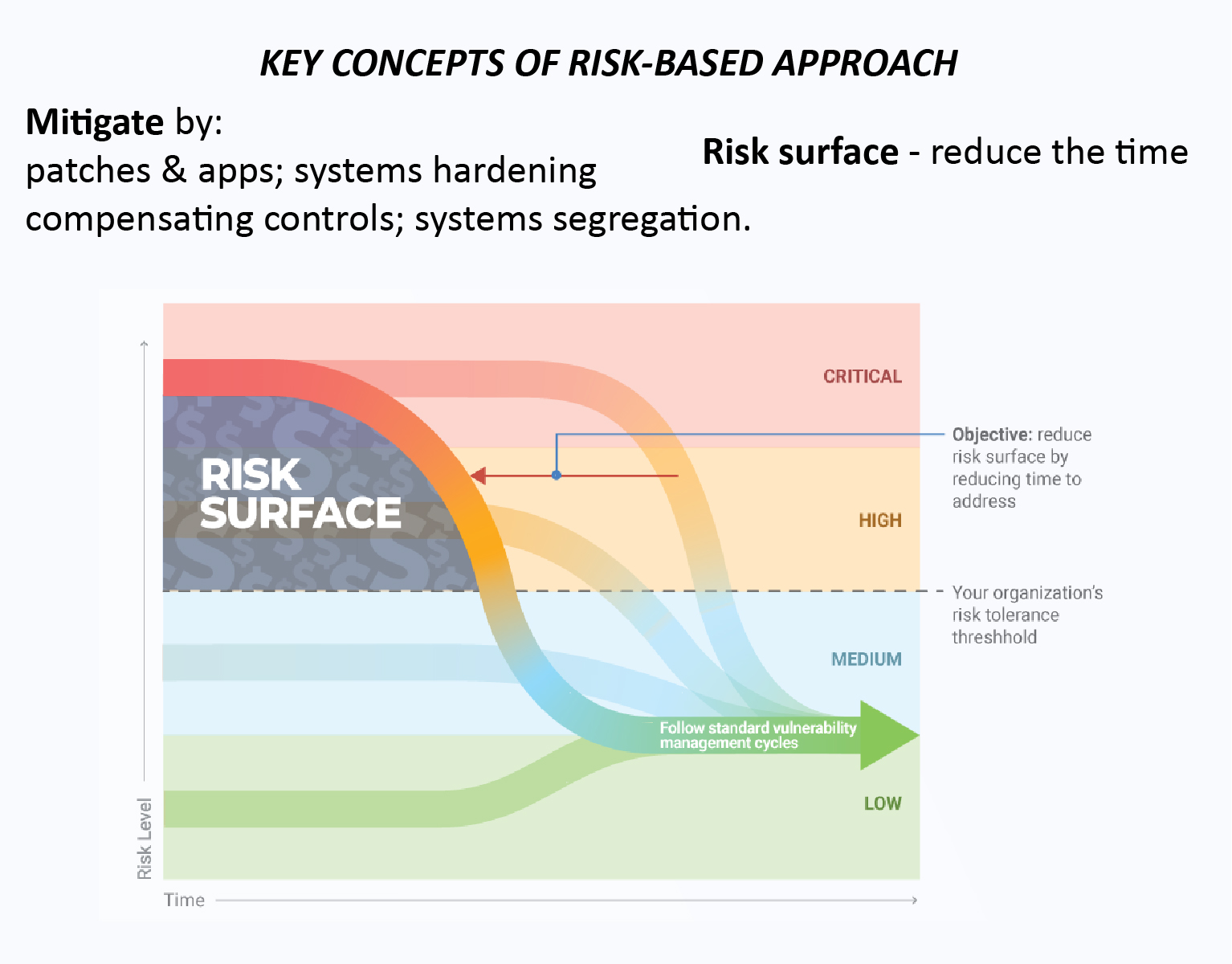
The key is having visibility over corporate security postures and evolution over time. Having this visibility will enable your operations and development teams to work more closely with your security team to provide a clear audit of everything that’s happening.
SANDLINE and its powerful tool CENTRAEYEZER can use the best of DevSecOps to:
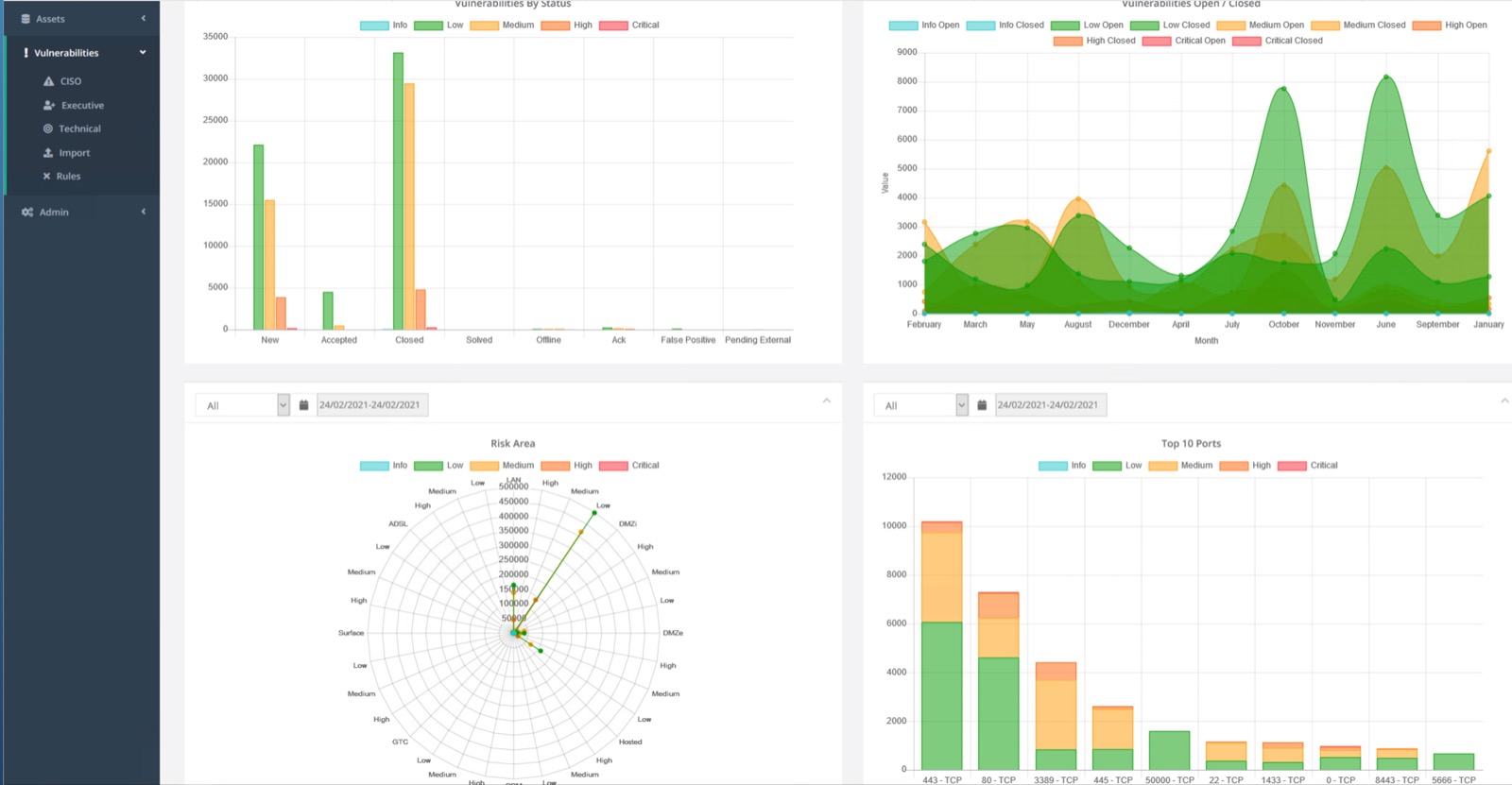
- Overview of your whole risk security posture.
- Monitoring the vulnerabilities of different environments (dev., QA, prod. etc.) by a large prioritization adaptability.
- Flexible job scheduling and orchestration.
- Prove compliance.
CONTACT US AND LET’S TALK!